iptables
2013-05-30 by dongnan
表和链
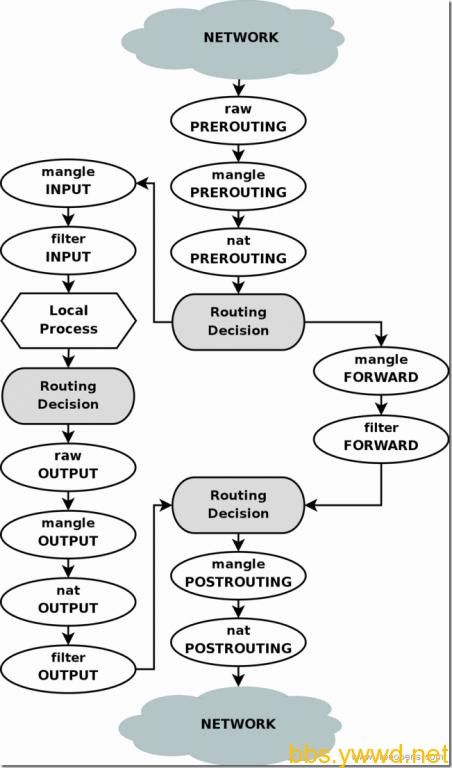
包含以下表和链:
- 4个表:
filter、nat、mangle、raw。 - 5个链:
PREROUTING、INPUT、FORWARD、OUTPUT、POSTROUTING。
表的优先级(由高到低)顺序为:
- raw
- mangle
- nat
- filter
例如,在PRROUTING链上,即有mangle表,也有nat表,那么先由mangle处理,然后由nat表处理。
举个栗子
基本操作
添加规则
iptables -t nat -A PREROUTING -d 1.1.1.2 -p tcp --dport 9000 -j DNAT --to-destination 192.168.1.99:9000
iptables -t nat -A POSTROUTING -p tcp -d 192.168.1.99 --dport 9000 -j SNAT --to-source 192.168.1.1
删除规则
iptables -t nat -D POSTROUTING -p tcp -d 192.168.1.99 --dport 9000 -j SNAT --to-source 192.168.1.1
# 也可以根据规则行号删除规则,获得行号参考下面的查看规则。
iptables -t nat -D PREROUTING 1
查看规则
# 带有规则行号 --line-numbers
iptables -t nat -L -n --line-numbers
本机端口重定向
REDIRECT 用于配置本机端口重定向,例如,将9000端口重定向到80端口:
iptables -t nat -A PREROUTING -p tcp --dport 9000 -j REDIRECT --to-ports 80
如果需要在本机访问新印射的端口,还得加个OUTPUT链规则:
iptables -t nat -A OUTPUT -p tcp --dport 9000 -j REDIRECT --to-ports 80
外网访问需要经过PREROUTING链,但是localhost不经过该链,因此需要用OUTPUT,或者POSTROUTING。
取反规则
感叹号"!",表示取反。这条规则的意思是除了规定的ip 地址外,其它ip 连接22端口全部拒绝:
iptables -I INPUT -p tcp ! -s your_ip --dport 22 -j DROP
匹配字符串
匹配外部访问本机TCP协议25端口并且字符串含有baidu.com的数据包,拒绝通过:
iptables -I INPUT -p tcp --dport 25 -m string --string ".baidu.com" --algo bm -j DROP
匹配状态
目标为本机,TCP状态为 RELATED,ESTABLISHED的允许通过,为 INVALID 则拒绝通过:
iptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -A INPUT -m state --state INVALID -j DROP
LIMIT 限制模块
limit 仅是个 match 模块,他的功能是匹配,匹配方式是按一定平均速率 ,至于“拒绝”还是“允许”是后面 -j 动作来决定。
iptables -A INPUT -p icmp -m limit --limit 10/m --limit-burst 5 -j ACCEPT
iptables -A INPUT -p icmp -j DROP
- 第1条规则,前5个
imcp包正常通过,从第6个包开始,每6秒允许通过1个imcp包。 - 第2条规则,超过第一条规则的
icmp包拒绝通过。
icmp 类型
icmp类型:0 为回显应答 8 为回显请求
iptables -I INPUT -p icmp --icmp-type 8 -j ACCEP
iptables 脚本示例
根据需要自行添加删除规则:
#!/bin/bash
#
IPTABLES=/sbin/iptables
company1="218.241.x.x"
wan="211.151.x.x/27"
lan="10.0.x.x/24"
$IPTABLES -F
$IPTABLES -X
$IPTABLES -Z
$IPTABLES -F -t nat
$IPTABLES -X -t nat
$IPTABLES -Z -t nat
#$IPTABLES -P FORWARD DROP
$IPTABLES -P INPUT DROP
# Allow Office
$IPTABLES -A INPUT -d 224.0.0.18 -j ACCEPT #vrrp
$IPTABLES -A INPUT -i lo -j ACCEPT
$IPTABLES -A INPUT -s $lan -j ACCEPT
$IPTABLES -A INPUT -s $wan -j ACCEPT
$IPTABLES -A INPUT -s $company1 -j ACCEPT
# Allow Port
$IPTABLES -A INPUT -p tcp -s 0/0 --dport 80 -j ACCEPT
$IPTABLES -A INPUT -p tcp -s 0/0 --dport 443 -j ACCEPT
# ALLOW PING
$IPTABLES -A INPUT -i eth0 -p icmp -j ACCEPT
# Allow alive conn
$IPTABLES -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
# Deny ip
#$IPTABLES -I INPUT -s 202.116.102.7 -j DROP
raw表
raw表只使用在PREROUTING链和OUTPUT链上,因为优先级最高从而可以对收到的数据包在连接跟踪前进行处理。
一但用户使用了raw表,在某个链上raw表处理完后,将跳过nat表和 ip_conntrack处理,即不再做地址转换和数据包的链接跟踪处理了。
raw表应用在那些不需要做nat的情况下以提高性能。如大量访问的web服务器,可以让80端口不再让iptables做数据包的链接跟踪处理,以提高用户的访问速度。
使用raw表
增加raw表的规则,在其它表处理之前,使用"-j NOTRACK"跳过其它表,状态方面除了以前的四个状态还增加了一个 UNTRACKED 状态
指定进入80端口的数据包不再进行链接跟踪处理:
iptables -t raw -A PREROUTING -d 1.2.3.4 -p tcp --dport 80 -j NOTRACK
iptables -t raw -A PREROUTING -s 1.2.3.4 -p tcp --sport 80 -j NOTRACK
iptables -A FORWARD -m state --state UNTRACKED -j ACCEPT
命令帮助
NAME
iptables — administration tool for IPv4 packet filtering and NAT
SYNOPSIS
iptables [-t table] {-A|-C|-D} chain
iptables [-t table] -I chain [rulenum]
iptables [-t table] -R chain rulenum
iptables [-t table] -D chain rulenum
iptables [-t table] -S [chain [rulenum]]
iptables [-t table] {-F|-L|-Z} [chain [rulenum]] [options...]
iptables [-t table] -N chain
iptables [-t table] -X [chain]
iptables [-t table] -P chain target
iptables [-t table] -E old-chain-name new-chain-name
rule-specification = [matches...] [target]
match = -m matchname [per-match-options]
target = -j targetname [per-target-options]
DESCRIPTION
iptables is used to set up, maintain, and inspect the tables of IPv4 packet filter rules in the Linux kernel.
Several different tables may be defined. Each table contains a number of built-in chains and may also contain user-defined chains.
-t, --table table
This option specifies the packet matching table which the command should operate on.
If the kernel is configured with automatic module loading, an attempt will be made to load the appropri‐
ate module for that table if it is not already there.
filter
nat
mangle
raw
OPTIONS
The options that are recognized by iptables and ip6tables can be divided into several different groups.
-A, --append chain rule-specification
Append one or more rules to the end of the selected chain.
-D, --delete chain rule-specification
-D, --delete chain rulenum
Delete one or more rules from the selected chain.
-I, --insert chain [rulenum] rule-specification
Insert one or more rules in the selected chain as the given rule number.
So, if the rule number is 1, the rule or rules are inserted at the head of the chain.
This is also the default if no rule number is specified.
-L, --list [chain]
List all rules in the selected chain.
If no chain is selected, all chains are listed. Like every other iptables command,
it applies to the specified table (filter is the default), so NAT rules get listed by
iptables -t nat -n -L
-F, --flush [chain]
Flush the selected chain (all the chains in the table if none is given).
his is equivalent to deleting all the rules one by one.
-Z, --zero [chain [rulenum]]
Zero the packet and byte counters in all chains, or only the given chain, or only the given rule in a chain.
-X, --delete-chain [chain]
Delete the optional user-defined chain specified.
-P, --policy chain target
Set the policy for the chain to the given target. See the section TARGETS for the legal targets.
扩展模块:
man iptables-extensions
NAME
iptables-extensions — list of extensions in the standard iptables distribution
SYNOPSIS
iptables [-m name [module-options...]] [-j target-name [target-options...]
MATCH EXTENSIONS
iptables can use extended packet matching modules with the -m or --match options, followed by the matching module name;
after these, various extra command line options become available, depending on the specific module.
string
This modules matches a given string by using some pattern matching strategy. It requires a linux kernel >= 2.6.14.
--algo {bm|kmp}
Select the pattern matching strategy. (bm = Boyer-Moore, kmp = Knuth-Pratt-Morris)
[!] --string pattern
Matches the given pattern.