ssldump 命令
2015-12-07 by dongnan
举个栗子
正常SSL请求过程,借用F5官网上的图片。
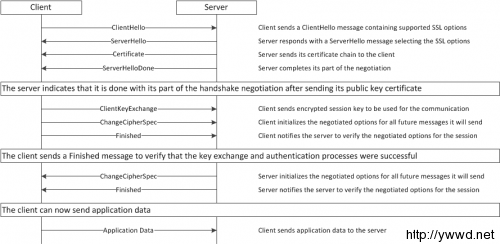
客户端
客户端发送请求
curl -k -H"Host:m.ywwd.net" https://58.83.1x.2x/payXXX
服务器端
服务器端使用 ssldump 抓包
# 执行命令
ssldump -i eth0 port 443 and host 114.242.1xx.93
# 返回结果
New TCP connection #1: 114.242.1x.2x(52215) <-> 58.83.1x.2x(443)
1 1 0.0192 (0.0192) C>S Handshake
ClientHello
Version 3.3
cipher suites
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
TLS_DHE_DSS_WITH_AES_256_GCM_SHA384
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
TLS_DHE_RSA_WITH_AES_256_CBC_SHA256
TLS_DHE_DSS_WITH_AES_256_CBC_SHA256
TLS_DHE_RSA_WITH_AES_256_CBC_SHA
TLS_DHE_DSS_WITH_AES_256_CBC_SHA
TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA
TLS_DHE_DSS_WITH_CAMELLIA_256_CBC_SHA
TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384
TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384
TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384
TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384
TLS_ECDH_RSA_WITH_AES_256_CBC_SHA
TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA
TLS_RSA_WITH_AES_256_GCM_SHA384
TLS_RSA_WITH_AES_256_CBC_SHA256
TLS_RSA_WITH_AES_256_CBC_SHA
TLS_RSA_WITH_CAMELLIA_256_CBC_SHA
TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA
TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA
TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA
TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA
TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA
TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA
TLS_RSA_WITH_3DES_EDE_CBC_SHA
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
TLS_DHE_DSS_WITH_AES_128_GCM_SHA256
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
TLS_DHE_RSA_WITH_AES_128_CBC_SHA256
TLS_DHE_DSS_WITH_AES_128_CBC_SHA256
TLS_DHE_RSA_WITH_AES_128_CBC_SHA
TLS_DHE_DSS_WITH_AES_128_CBC_SHA
TLS_DHE_RSA_WITH_SEED_CBC_SHA
TLS_DHE_DSS_WITH_SEED_CBC_SHA
TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA
TLS_DHE_DSS_WITH_CAMELLIA_128_CBC_SHA
TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256
TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256
TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256
TLS_ECDH_RSA_WITH_AES_128_CBC_SHA
TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_128_GCM_SHA256
TLS_RSA_WITH_AES_128_CBC_SHA256
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_SEED_CBC_SHA
TLS_RSA_WITH_CAMELLIA_128_CBC_SHA
TLS_EMPTY_RENEGOTIATION_INFO_SCSV
compression methods
NULL
1 2 0.0271 (0.0079) S>C Handshake
ServerHello
Version 3.3
session_id[32]=
7a 74 b2 15 20 96 8f a1 55 19 72 69 2a 7e cc d4
f3 fd 7a e0 b2 fd 56 03 08 6d e5 70 f7 ba 8f 28
cipherSuite TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
compressionMethod NULL
1 3 0.0272 (0.0000) S>C Handshake
Certificate
1 4 0.0272 (0.0000) S>C Handshake
ServerKeyExchange
Not enough data. Found 327 bytes (expecting 32767)
1 5 0.0272 (0.0000) S>C Handshake
ServerHelloDone
1 6 0.0498 (0.0226) C>S Handshake
ClientKeyExchange
Not enough data. Found 64 bytes (expecting 16384)
1 7 0.0498 (0.0000) C>S ChangeCipherSpec
1 8 0.0498 (0.0000) C>S Handshake
1 9 0.0514 (0.0016) S>C ChangeCipherSpec
1 10 0.0514 (0.0000) S>C Handshake
1 11 0.0702 (0.0188) C>S application_data
1 12 0.0775 (0.0072) S>C application_data
1 13 0.0959 (0.0183) C>S Alert
1 0.0959 (0.0000) C>S TCP FIN
1 14 0.0960 (0.0000) S>C Alert
1 0.0961 (0.0000) S>C TCP FIN
命令帮助
NAME
ssldump - dump SSL traffic on a network
SYNOPSIS
ssldump [ -vTshVq -aAdeHnNqTxXvy ] [ -i interface ]
[ -k keyfile ] [ -p password ] [ -r dumpfile ]
[ -S [crypto|d|ht|H|nroff] ] [ expression ]
DESCRIPTION
ssldump is an SSL/TLS network protocol analyzer. It identifies TCP connections on the chosen network interface and attempts to interpret them as SSL/TLS traffic. When it identifies SSL/TLS traffic, it decodes the records and displays them in a textual form to stdout. If provided with the appropriate keying material, it will also decrypt the connections and display the application data traffic.
-i interface
Use interface as the network interface on which to sniff SSL/TLS traffic.
小结
使用 ssldump 工具了解 ssl握手流程,对于排错有很大帮助。